Open source platform for X.509 certificate based service authentication and fine grained access control in dynamic infrastructures
Never Trust &
Always Verify
Enables zero trust core principles like traffic encryption, AuthN, AuthZ, Dynamic Trust and least privilege access
Learn More
X.509 Certificate Based Authentication
Service identity in the form of short-lived X.509 certificates to all workloads deployed in private or public clouds
*How is Athenz different from SPIRE?
Learn More
Fine-grained Authorization
Authorize all authenticated clients using fine-grained role-based (RBAC) access control with industry standard JWT access tokens
Learn More
Problem
How to enable Zero Trust core principles like traffic encryption and authentication among all workloads in a hybrid environment?
Solution
Athenz issues service identities in the form of short-lived X.509 certificates to all workloads deployed in private or public clouds enabling secure communication among all workloads with mTLS.
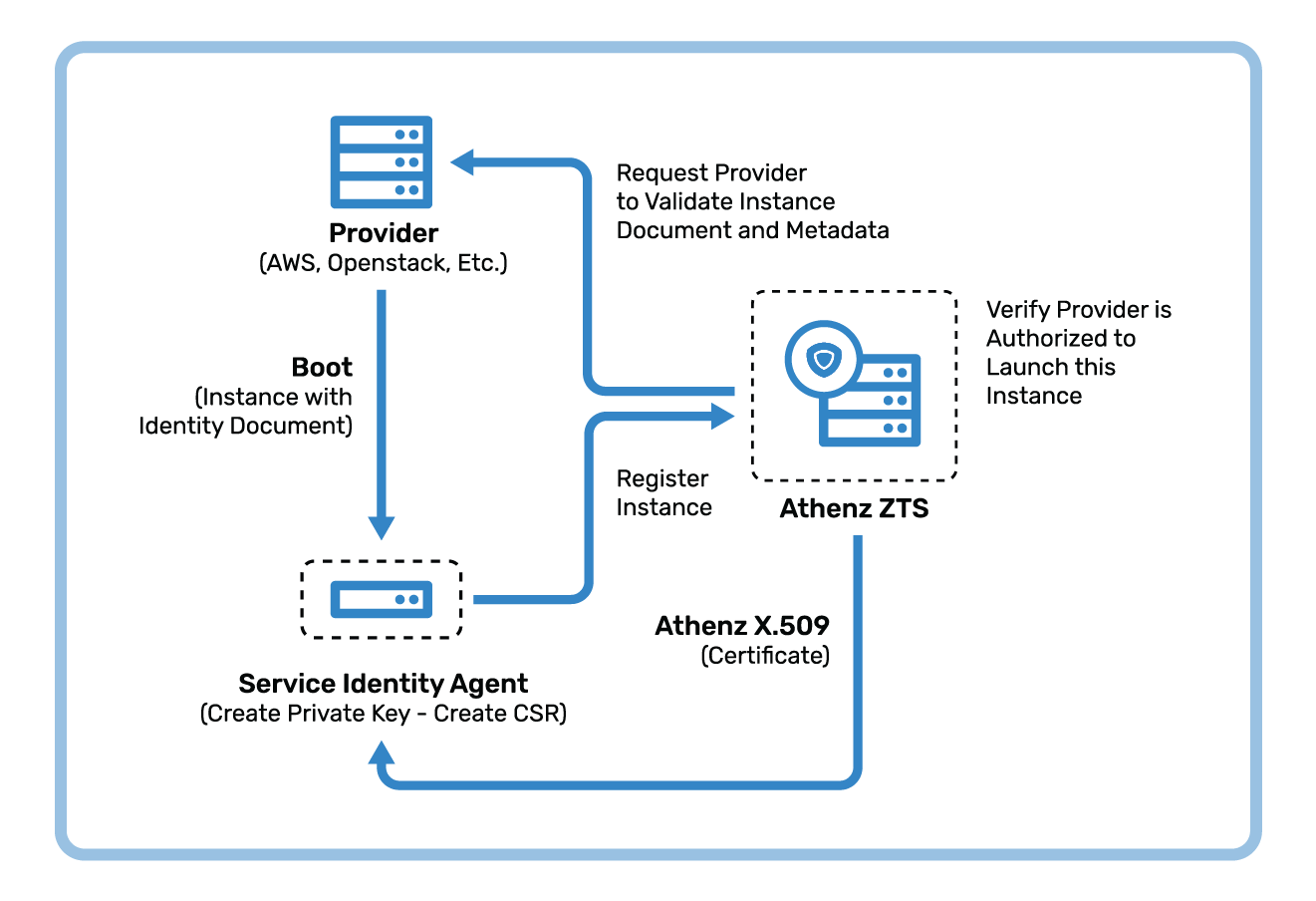
Problem
How do we provide credentials to container workloads to prove its identity and to authenticate with the Kubernetes API, establish mTLS with services, and define role-based access control (RBAC)?
Solution
An Identity provider mechanism enables workloads to authenticate with kubernetes container credentials such as pod bound service account tokens in exchange for Athenz service identity certificates using a callback mechanism that allows a kubernetes pod-aware identity service to authenticate such credentials.
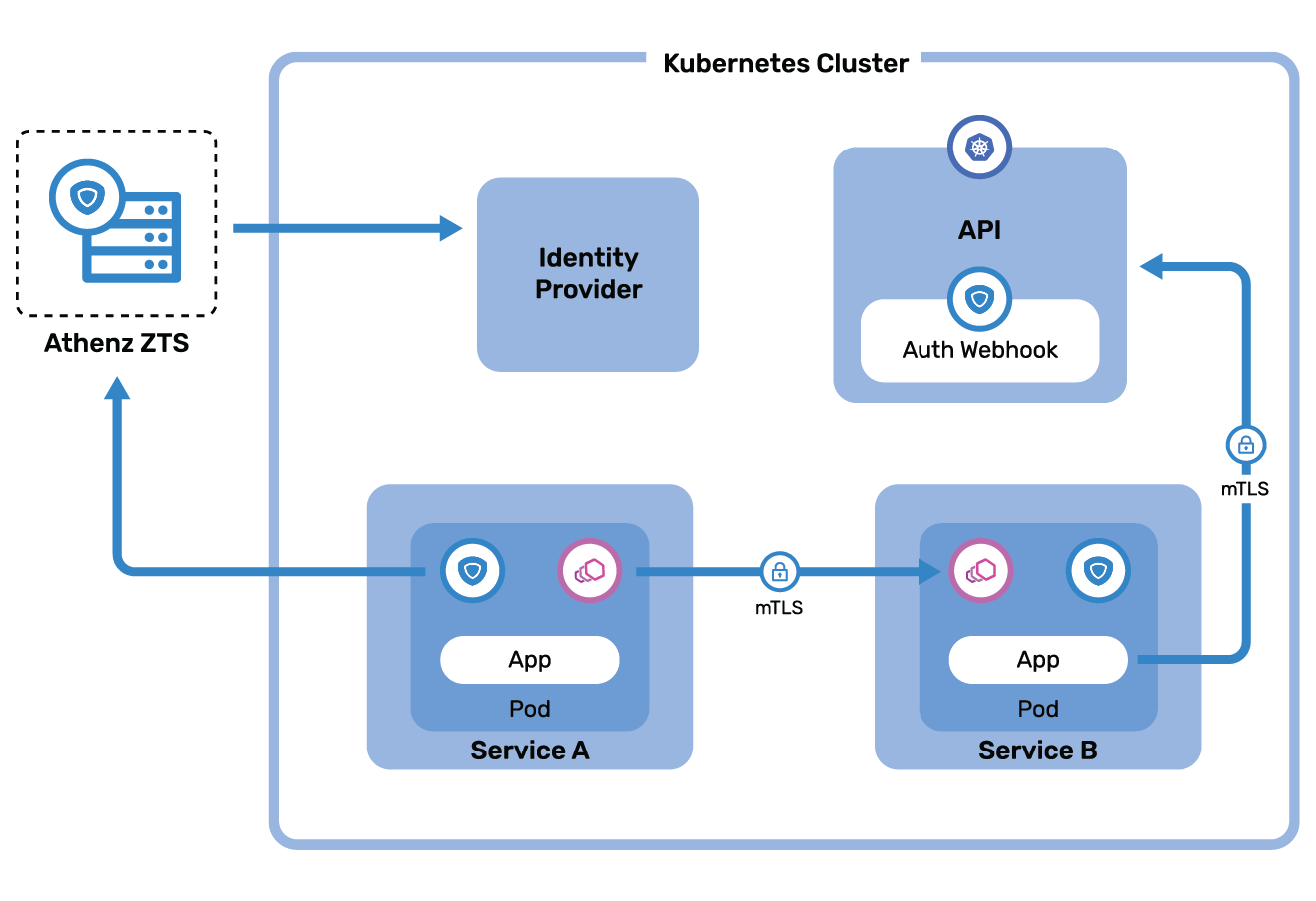
Problem
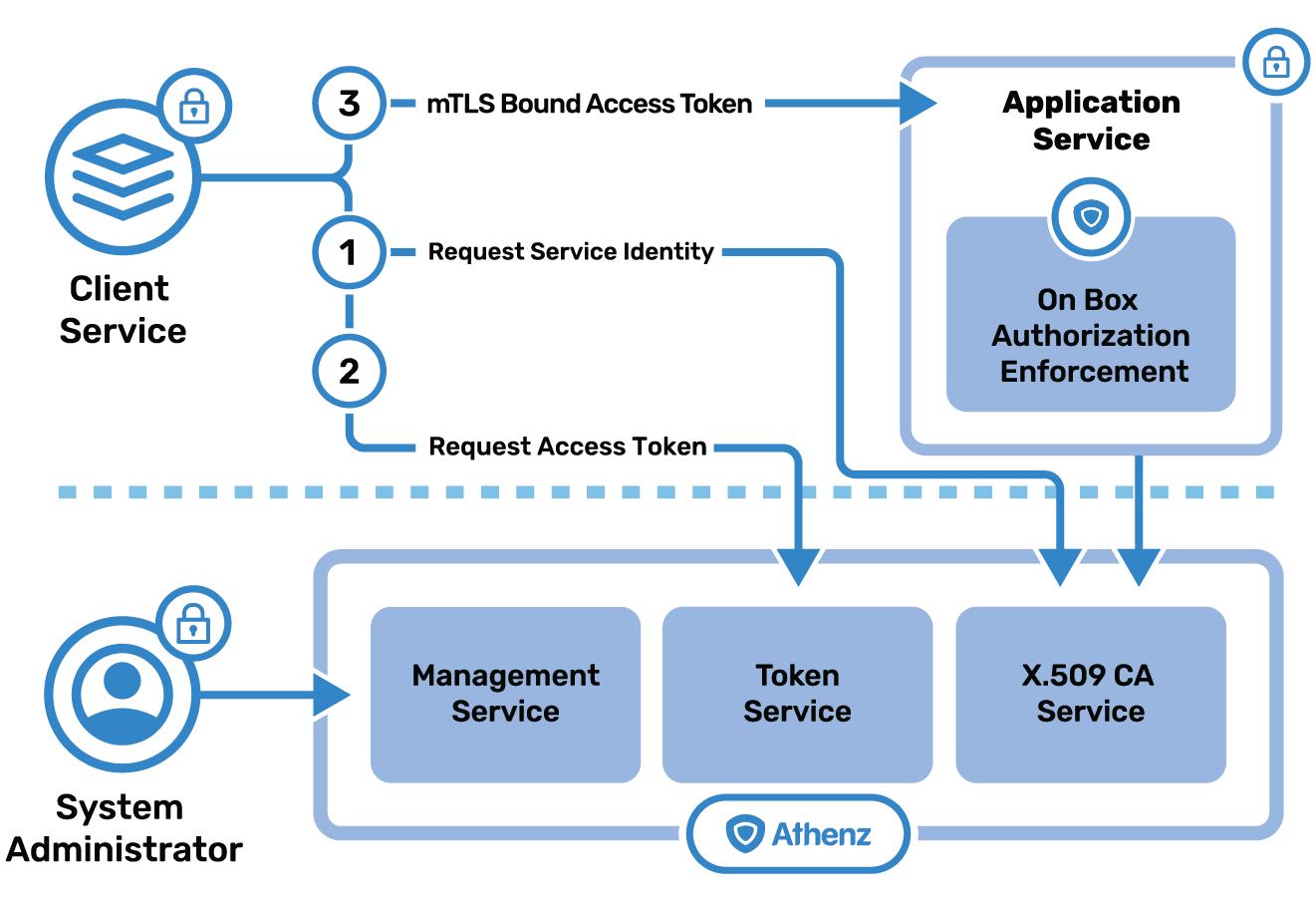
How to deploy a centralized authorization store and deploy a consistent authorization solution based on industry standard OAuth2 access tokens without implementing the logic in each application?
Solution
Athenz Token Service issues industry standard mTLS bound OAuth2 access tokens that application services can use to both authenticate (x.509 identity certificates) and authorize requests based on policies defined in the Athenz Management System.
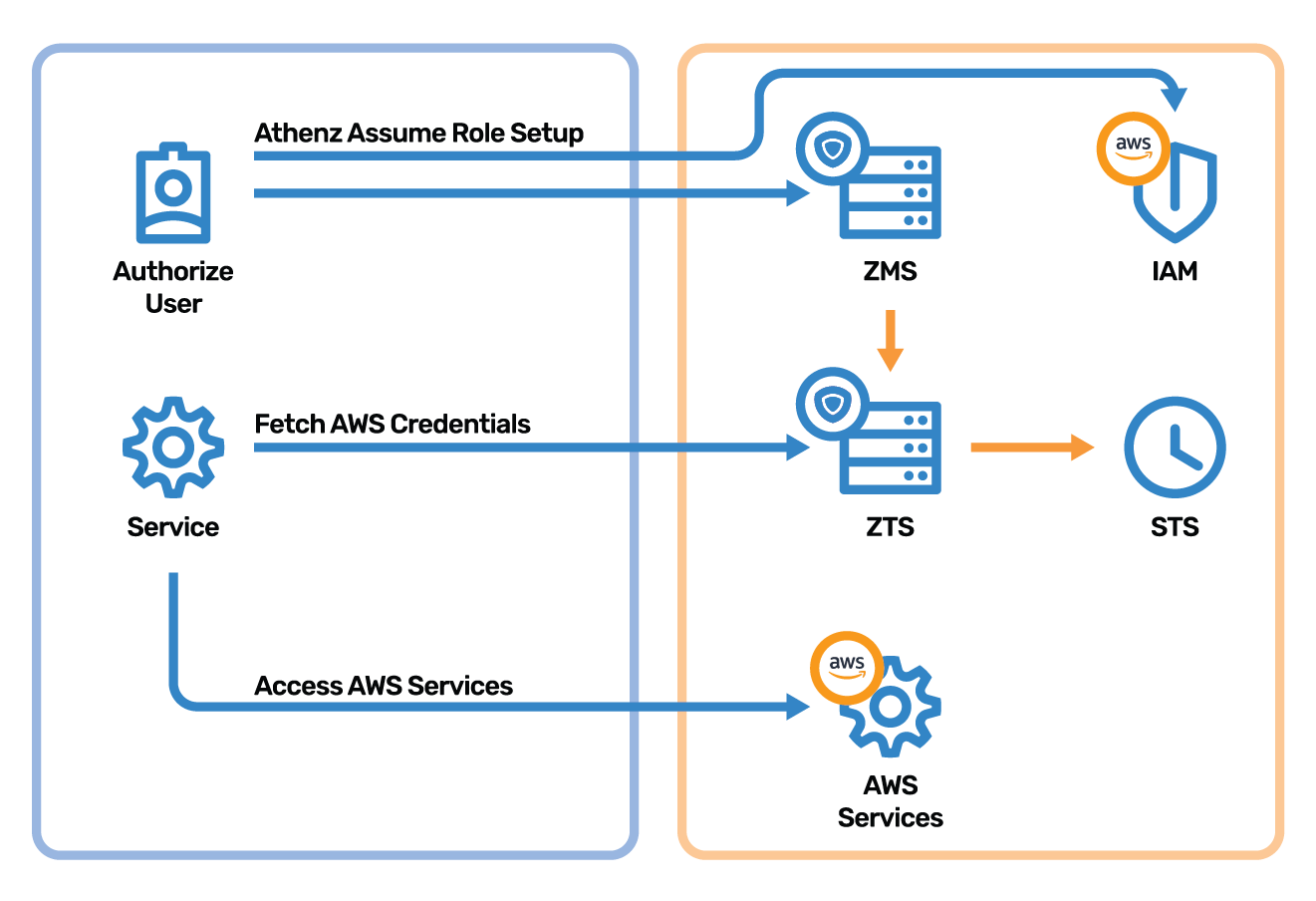
Problem
How to securely access AWS services from on-prem data centers without using static credentials defined in AWS IAM?
Solution
Services running in on-prem data can use their Athenz issued identity x.509 certificates to request AWS temporary credentials from Athenz Token Service running in AWS.